But what does it even mean, and how does it actually work? Or does it actually work? Well, we’re sure you have all of these questions in mind. Hence, we’ve written this piece to help you find answers, and understand the concept of encryption. Let us begin. Firstly, let us understand what encryption and decryption mean.
Understand the Basics of Encryption
Encryption means converting information into a code, which hides the true meaning of the information. Decryption means converting this code, back to the original information and giving back its meaning. It is the reverse mechanism of encryption.
However, to truly understand it, we obviously need more context.
Why Do You Need Encryption
When you send something online, be it a message, a comment, or an image – they carry some ‘information’. That is, if you send a message to me, I will be able to interpret the information you are trying to convey. Similarly, if you are sending an image to me, I will be able to see and interpret the contents of the image. What we need to understand, is that this message or image is not valuable by itself – but, is valuable for the information it provides. It is valuable for the information one can interpret as one sees it. Now, what if the message or the image you are sending, is also seen by someone else other than me over the internet? They get to know the information you are trying to convey, and this is a concern because you only intend it to be interpreted by me. So, how about using encryption and decryption? Exactly – and this is where end-to-end encryption comes in.
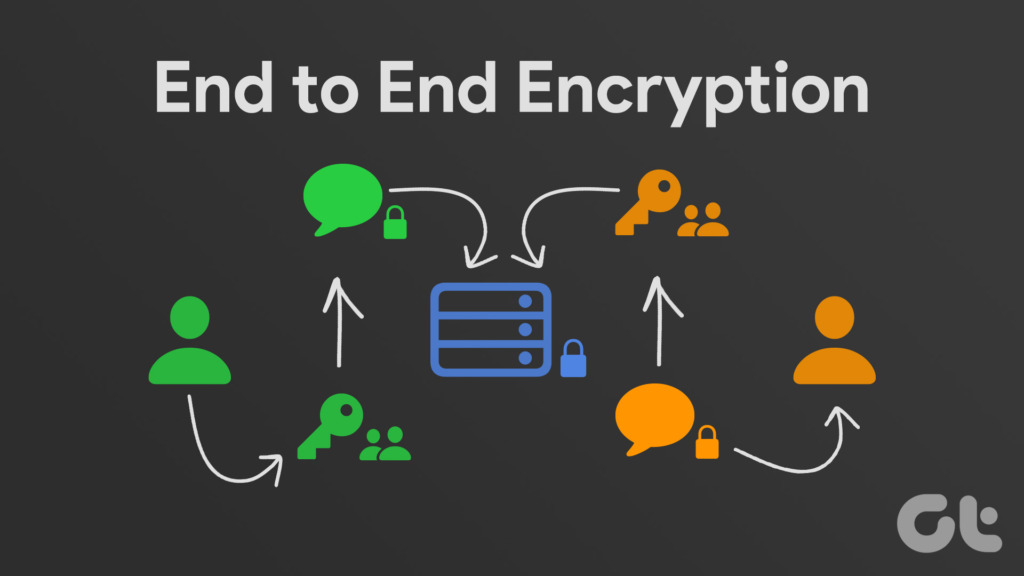
What is End-to-End Encryption
You encrypt the message/image you are trying to send, and it passes over the internet as a ‘secret’ code. And it’s done in such a way, that only I will be able to decrypt this ‘secret’ code. Therefore, once it reaches me, I will be able to decrypt and interpret this information. However, as mentioned earlier, what matters is the meaning in the end. So, it is ok to pass the message/image as secret codes from the sender to the receiver. This process is called end-to-end encryption. In the simplest terms, end-to-end encryption ensures secret communication between the sender and receiver, preventing third parties from accessing this information. The tools and technologies, that help us perform this process are engineered into messaging apps and other software that we (may) use. Let’s dive deep into this.
How Does End-to-End Encryption Work
We’re clear about the goal of end-to-end encryption – which is to prevent any intruders from stealing information between the sender and the receiver. Now, let us understand this concept through a situation, which we used earlier – you are sending me a message. When we use an end-to-end encryption service, it provides us with a public and a private key pair. These keys help us in encryption and decryption. Along with this, the messaging app has an algorithm, that consists of mathematical functions that have to be solved – to either encrypt or decrypt the data. When you are sending me a message, you will be provided a public key that is mapped to my chatbox. The public key is used to encrypt the message, using the algorithm present in the messaging app. This public key helps you recognize my device and the fact that I should receive the message. Now, I will use the private key, which helps me decrypt the message, and interpret the information of the message, sent by you. This private key is only available and exclusive to my device. Hence, nobody else will be able to decrypt the message – hence, making the end-to-end encryption successful. This is the fundamental operating principle of end-to-end encryption. However, if you would want to know more, we recommend you dive deep into the concepts of cryptography. However, not all services use end-to-end encryption. Some commonly use transport layer encryption instead. So, let us understand the differences between the two.
End-to-End Encryption vs. Transport Layer Security Encryption
As mentioned earlier, not all services are end-to-end encrypted. But, that does not mean that they do not have any means of encryption at all. The most common form of encryption for websites is the TLS – Transport Layer Security encryption. The only difference between this, and end-to-end, is that in TLS, the encryption takes place in the sender’s device, and gets decrypted at the server. Hence, it is not truly end-to-end encrypted but offers a good degree of securing and safeguarding your information. It is also called encryption in transit. This means that the service provider can access all of your messages through their servers. That is why you can easily see your old Instagram messages when you freshly download the app, but not on WhatsApp. You can only restore messages by downloading the backup file and decrypting it on your device. Now that we have a clear idea about end-to-end encryption, let us learn about the key advantages and disadvantages.
Advantages and Disadvantages of End-to-End Encryption
Here are some of the advantages of end-to-end encryption.
Every step of the way is fully protected.The servers of messaging services cannot access messages and related information.Information cannot be accessed by unauthorized people online. You cannot restore messages through a fresh sign-in – unless there is an encrypted backup. Consider the example of Instagram messenger and WhatsApp Messenger explained above.
Here are some disadvantages of end-to-end encryption.
Metadata such as date, time, and participant names are not encrypted. If the endpoints (sender or receiver) are vulnerable to an attack, there is only little that end-to-end encryption can do. In some cases, a man in the middle attack is possible despite having end-to-end encryption. Therefore, if someone chooses to impersonate the sender or the receiver physically, the messages and the information can be read by unintended people.
So, these were all the pros and cons of end-to-end encryption. If you’re still wondering whether to enable end-to-end encryption even if you don’t send secret messages, the answer is a resounding YES. Why let others access your data at all? So, if you’re planning to use this service, the next section elaborates on which popular messaging services provide end-to-end encryption.
Popular End-to-End Encrypted Messaging Apps
Here are some of the best end-to-end encrypted messaging apps for iPhone and Android. You can use any of the below to add a layer of security to your messages.
1. WhatsApp Messenger
The ever-so-popular WhatsApp messenger supports end-to-end encryption. You can use the below links to download and install for both iPhone and Android. Download WhatsApp for iPhone Download WhatsApp for Android
2. Signal Private Messenger
Signal is another feature-rich, end-to-end encrypted messenger for iPhone and Android. We feel it provides a more modern-looking user interface in comparison to WhatsApp. Download Signal for iPhone Download Signal for Android
3. iMessage
iMessage, as we all know is the vanilla messaging app for all Apple users. All messages and files on iMessage are end-to-end encrypted. However, it does not work via cross-platforms and hence, is not available for Android.
4. Telegram
Telegram is another feature-rich messenger, that all of us want to use as a primary messaging app, and wish for all WhatsApp users to migrate to it. It offers end-to-end encryption, albeit on an optional basis. This option is called ‘secret chat’. Download Telegram for iPhone Download Telegram for Android
Ensure Private Messaging With End-to-End Encryption
This is all you need to know about end-to-end encryption. We hope you found this article easy to understand. Now, the next time you see a banner that says ‘your messages are end to end encrypted’ – you know what it means! The above article may contain affiliate links which help support Guiding Tech. However, it does not affect our editorial integrity. The content remains unbiased and authentic.